Step up to the world of internet & technology with darkweb developers, Get access to our premium services for free, We Provide Services on Android Development, SEO, Web Traffic, Web development and other technical services, Feel free to ask us. Contact : +15053980423 email: darkwebdevelopers@gmail.com
Monday, 15 October 2018
Thursday, 7 June 2018
Artificial Intelligence
Artificial Intelligence :
There is a lot of buzz around these days, about the artificial intelligence, and the term AI seems to be thrown around a lot, but what is it exactly ? 🧐
First of all, lets look at the definition
To avoid confusion we have to go back to the earliest and hence purest
definition of AI was first coined by Jay McCartney in 1955 at Dartmouth Conference.
Of course those plenty of research work done on AI by others such before this, but what they were working on was an undefined field before 1955.
Okay so here's what McCarthy proposed
" Every aspect of learning or any other feature of Intelligence can in principle be so precisely described that a machine can be made to simulate it.An attempt will be made to find how to make machines use language, from abstractions and concepts, solve kind of problems now reserved for humans, and improve themselves"
AI is a machine with the ability to solve problems that are usually done by humans with our natural intelligence
A computer would demonstrate a form of intelligence when it learns how to improve itself at solving these problems
To elaborate further, the 1955 proposal defines 7 areas of AI.
Today there are surely more but here are the original 7
- Simulating higher functions of the human brain.
- Programming a computer to use general language.
- Arranging hypothetical neurons in a manner so that they can form concepts
- A way to determine and measure problem complexity
- Self-improvement.
- Abstraction: Defined as the quality of dealing with ideas rather than events.
- Randomness and creativity.
So in the definition, you can see the word "Intelligence"
now, what is intelligence ?
Well! according to Jack Copeland, Who has written several books on AI, Some of the most important factors of intelligence are
- Generalization learning: that is learning that enables the learner to be able to perform better in situations not previously encountered
- Reasoning: to reason to draw conclusions appropriate to the situation in hand
- Problem solving: given such and such data find x
- perception: analyzing an environment features and relationships between objects.
- Language Understanding : Understanding a language by following syntax and other rules similar to a human
Okay, So now we have an understanding of AI and Intelligence,
now lets bring it together a bit and solidify the concepts in your mind of what AI is here's few example of AI
Machine Learning, Computer Vision, Natural language processing, Robotics, Pattern recognition and knowledge management
there are also different kind of Artificial Intelligence in terms of approach.
For example : Strong AI & Weak AI
Strong AI: It is a system formed by simulating the human brain by building systems that thinks and the process, give us an insight into how the brain works ( we are nowhere near the stage yet 😅)
Weak AI: It is a system that behaves like a human but doesn't give us a insight into how the brain works ,
IBM's Deep Blue a chess playing AI was an example of it.
It processed millions of moves before it made any actual moves on the chessboard,
Weak AI achieves only the result of a human not the actual process
It doesn't stop here either..
there is actually a new kind of middle ground between Strong and Weak AI
this is where a system is inspired by human reasoning but doesn't have to stick to it !!!
IBM's Watson is an example of it
( Like humans it reads a lot of information recognizes patterns and builds up evidence to say, " hey I am x percent confident that this is the right solution to the question that you have asked me from the information that I have read ")
Google's deep learning is similar as it mimics the structure of the human brain by using neural networks but doesn't follow its function exactly,
the system uses nodes that acts as artificial neurons connecting information.
Going a little bit deeper, neural networks are actually a subset of machine learning, So !! what's machine learning then ??
Machine learning refers to algorithms that enable software to improve its performance over the time, as it obtains more data about usage pattern.
Strong AI: It is a system formed by simulating the human brain by building systems that thinks and the process, give us an insight into how the brain works ( we are nowhere near the stage yet 😅)
Weak AI: It is a system that behaves like a human but doesn't give us a insight into how the brain works ,
IBM's Deep Blue a chess playing AI was an example of it.
It processed millions of moves before it made any actual moves on the chessboard,
Weak AI achieves only the result of a human not the actual process
It doesn't stop here either..
there is actually a new kind of middle ground between Strong and Weak AI
this is where a system is inspired by human reasoning but doesn't have to stick to it !!!
IBM's Watson is an example of it
( Like humans it reads a lot of information recognizes patterns and builds up evidence to say, " hey I am x percent confident that this is the right solution to the question that you have asked me from the information that I have read ")
Google's deep learning is similar as it mimics the structure of the human brain by using neural networks but doesn't follow its function exactly,
the system uses nodes that acts as artificial neurons connecting information.
Going a little bit deeper, neural networks are actually a subset of machine learning, So !! what's machine learning then ??
Machine learning refers to algorithms that enable software to improve its performance over the time, as it obtains more data about usage pattern.
Our page has been shifted to new wordpress site Darkweb developers
Monday, 21 May 2018
SEO: the killer way to sky-rocket your traffic
SEO: ( Search Engine Optimization )
- The killer way to sky-rocket your traffic
Have you ever wondered how websites end up on page one in Google !!!
But why your site isn’t listed there??
Do they pay for that ? or they know someone from google actually? is it luck ???
or it just happens !!
Nooo !! Of course Not !!!!!
-Then ?
Are there actual techniques? that can help to get to 1st Page of Google ???
The good news is: Yes !!! there are... .
The Art of Ranking well in search engines is called SEO ( Search Engine Optimization ) and people who do it well, make a lot of Money!
 |
| SEO : Darkweb Developers |
Wednesday, 9 May 2018
IOT: Internet Of Things or Internet On threats
IOT: Internet Of Things
Internet of Things ? or Internet On Threats ?
Over the last few years, our demand of making life easier is been growing, and since then things are being interconnected for the ease of life
We have already stepped into a world where things are connected,
your smartphone your tv your fitness band all are in sync simultaneously .
your smartphone your tv your fitness band all are in sync simultaneously .
In distant future there is even possibility that your door lock will be accessible with your smart phone!! there will no need of any physical key,
the world will be unified into a single thing,
everything will be connected to each other, your home, your car, your switch board, your shower, even your fans & bulbs !!
That's the internet of things (IOT)
(the interconnection via the Internet of computing devices embedded in everyday objects, enabling them to send and receive data.)
the idea of internet of things aren't that new, its about 3-4 decades old, but it takes time to implement ideas,
due to technological achievement this is possible today, but still its expensive to implement,
but the problem isn't that !!
if even we able to successfully implement technology, still there is a another big flaw which could be fatal, that's security threat !!!!
As your house hold things are connected to internet
it becomes more vulnerable.. .
Saturday, 5 May 2018
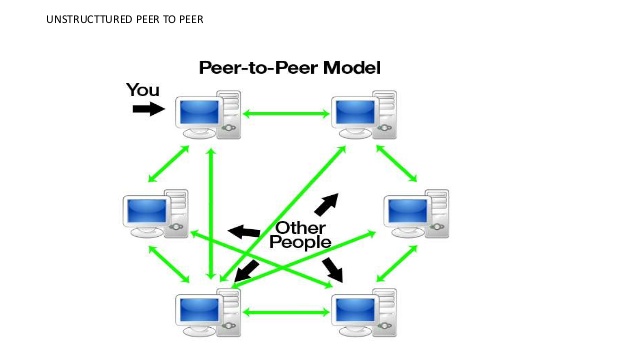
Peer to Peer (P2P) Communication
Peer to Peer (P2P) Communication
P2P computing or networking basically works on the basis of distributed application architecture,
Client server model is the basic model for that type communication, and before going to P2P we first try to understand it
The Client-Server model of Computing is a distributed application structure that partitions tasks or workloads between the providers of a resource or service called servers and service requesters are called clients
 |
| Photo Credit:slideshare.net |
Now lets move to P2P
Unlike Client-Server model here every nodes acts like client as well as server, where a workload or any process is distributed among peers, and each peer is equally privileged,
In P2P networking each peers are the equipotent participants in any work process forming a peer to peer (P2P) network of Nodes.
P2P CAN USED TO PROVIDE ANONYMIZED ROUTING OF NETWORK TRAFFIC MASSIVE PARALLEL COMPUTING ENVIRONMENTS, DISTRIWTED STORAGE AND OTHER FUNCTIONS, MOST P2P ARE FOCUSED ON MEDIA SHARING AND P2P THERFORE OFTEN ASSOCIATED WITH SOFTWARE PIRACY AND COPYRIGHT VIOLATION.
What is Torrent ® & how does Torrent ® works
( Torrent ®: Gateway to Peer to Peer Sharing )
If you are one of them who often download movies, games from internet you might be familiar with the word torrent®, but do you know ? how does it actually works ? from where you do get your desired file which you can't find anywhere else ??
Torrent®
 |
Darkweb Developers
|
it is an internet based peer to peer file sharing protocol in a decentralized fashion, which works basically on the basis cloud computing technology,
where Basically, what happens, a person (seed) puts a file onto the torrent site and others can download this. Your peers will be people who are downloading the same thing you are downloading at that moment.
It is common curtsy to leave the item to upload so that others can load the file off you.
It is common curtsy to leave the item to upload so that others can load the file off you.
or In simple terms, When you are downloading something from torrent, actually you are just downloading a file from someone else's computer (seeder) & at the same time you are also acting as a seeder of the part of file which you have already downloaded, this means everyone who is downloading that file is acting as a small server for that particular file, that is how a file is being provided to multiple people efficiently,
You might have noticed, more the seeds more the download speed,
and now you understand why this happens !!
Sunday, 29 April 2018
Getting Started with Android Studio
Getting Started: Android Studio
A journey towards android development
 |
| Android Studio by darkweb developers |
Android is one of those mostly used mobile platform which is being used globally, & most probably the most popular one,
if u are reading this blog on a mobile, it is quite possible that it is also an android device.
Every time whenever you need any app to run on your device,
you simply hit install button on the google play store & enjoy its juice, but did you ever wondered ? from where did these app came from? of-course someone made those!!
but how ? how they did it ? Can you also do it ??
Interested?? Great !!! then go ahead and read out it all .. .
Most of the apps you see in play store is made with android studio,
yes there are some other platforms too! which allows android application development, But Android studio is Google's own product, & preferred by most of the developers,
We recommend Android studio over other 3rd Party Sources like AppsGeyser,
Well, Now how to make android application on android studio ??
I will teach you ! don't worry..
Now Its time to make some android application using android studio
Now Step By Step we will Learn about Android Studio
Now Step By Step we will Learn about Android Studio
#1 Introduction & installation of java SDK
#2 How to install Android Studio
#3 Building Your 1st android app ( hello world example )
Saturday, 14 April 2018
Tor Browser
[ TOR: The Onion Router ]
Tor Browser is the name of another interesting browser, which obviously comes into mind when your concern is dark web & online anonymity, its a great tool, which lets you to surf the internet through 5 layers of IP protection with superior anonymity, it protects your privacy greatly, though its not full proof.
History Of TOR: In the time of mid 1990's, Paul Syverson, Michael G. Reed & David Goldschlag Of United States Naval Research Laboratory, developed the core principle of TOR, with the purpose of protecting US Intelligence online. Later it was modified a lot & finally it was available for public use on 13th August 2004.
How Does the TOR works: Unlike other browser, its working mechanism isn't that much straight forward, it uses several layers of Virtual locations Using Various servers located at different location of globe, which more over works like multiple VPN
Usually, when you surf the internet, you first connect to your Internet Service Provider (ISP), which then redirects you to any other websites (or other content) that you wish to visit. in that case, all your internet traffic passes through your ISP’s servers, and can be viewed by them, & also can be traced by some other unwanted intruders, so here your anonymity gets hampered.
But When you are using TOR's multiple layer distributed VPN, Your information is send through an encrypted tunnel, to the servers of TOR located at anywhere in globe.This means that all data transmitting between your device and the VPS (Virtual Private Servers) of TOR is encrypted by several layers of protections so that your anonymity won't get hampered by unwanted intruders.
It’s anonymous - Nobody can ever track you down. (Location/Identity)
It’s safe - There is JavaScript protection for XSS/malicious code
It’s free - You don’t have to buy anything
Cons:
It’s very slow (compared a normal browser)
Scripts that can run are limited (due to JavaScript protection). In order to do some things, you might have to risk a little bit of your security.
Usually, when you surf the internet, you first connect to your Internet Service Provider (ISP), which then redirects you to any other websites (or other content) that you wish to visit. in that case, all your internet traffic passes through your ISP’s servers, and can be viewed by them, & also can be traced by some other unwanted intruders, so here your anonymity gets hampered.
But When you are using TOR's multiple layer distributed VPN, Your information is send through an encrypted tunnel, to the servers of TOR located at anywhere in globe.This means that all data transmitting between your device and the VPS (Virtual Private Servers) of TOR is encrypted by several layers of protections so that your anonymity won't get hampered by unwanted intruders.
Pros. & Cons. of TOR :
Pros.It’s anonymous - Nobody can ever track you down. (Location/Identity)
It’s safe - There is JavaScript protection for XSS/malicious code
It’s free - You don’t have to buy anything
Cons:
It’s very slow (compared a normal browser)
Scripts that can run are limited (due to JavaScript protection). In order to do some things, you might have to risk a little bit of your security.
Source: By Electronic Frontier Foundation, minor modifications by me. - https://www.torproject.org/about/overview.html.en, CC BY 3.0, https://commons.wikimedia.org/w/index.php?curid=17887560
https://darkwebdevelopers.blogspot.com
Saturday, 7 April 2018
Cryptocurrency
CryptoCurrency : A All New Trend
Having any Cryptocurrency is been a new trend these days, most of the people these days interested about, talking about, they are investing over it, buying it, selling it or even mining it.. etc. etc.
But, What are Cryptocurrencies ?
These are the digital assets, which were made for, to be used as a medium of exchange, alternate to actual money.
They can also be called as digital currencies or virtual currencies.
These are the decentralized currencies, unlike those centralized currencies they don't have any central authority, Cryptocurrencies uses decentralized control, The decentralized control of each cryptocurrency works through Block-chain, which is a public transaction database, functioning as distributed ledger ( Permanent summary of all individual transactions by date)
7 Most Important Cryptocurrencies
- Bitcoin
- Litecoin (LTC)
- Ethereum (ETH)
- Zcash (ZEC)
- Dash
- Ripple (XRP)
- Monero (XMR)
From where to get Cryptocurrencies
Cryptocurrencies can be obtained by means of exchange of money or it can be mined also, or can be received as a means payment too,
there are many special web wallets to store them,
⏭ To be Continued.. .
⏩The 1st ever Cryptocurrency : Bitcoin (2009) Founder: Satoshi Nakamoto, ( it is the most successful cryptocurrency till date )
Wednesday, 4 April 2018
Getting Started: Dark web Deep web & Surface web
You might have noticed these days, People around are talking about Dark webs Deep webs Surface webs etc. etc.
do you know whats' the actual thing behind ?
The World Wide Web is mainly consists of 3 Parts
- Surface Web
- Deep Web
- Dark Web
Surface Web: It is the visible part of the world wide web which is available for general public, and searchable through standard search engines.
Here your all Social networking sites, YouTube, Wikipedia, Blogs comes under, its the normal web content which normal people takes in use.
and the content is mostly legal.
Deep Web: Its the Invisible web or hidden part of world wide web, which is not indexed by standard search engines for any reason
The content of the deep web is hidden behind HTTPS forms,
and includes many very common uses such as online banking, web mail, Office databases of any organization, Some Paid Contents etc. etc.
Content of the deep web can be located and accessed by a direct URL or IP address, and may require password or other security access pass.
The content of the deep web is hidden behind HTTPS forms,
and includes many very common uses such as online banking, web mail, Office databases of any organization, Some Paid Contents etc. etc.
Content of the deep web can be located and accessed by a direct URL or IP address, and may require password or other security access pass.
Dark Web: The dark web consists of contents which is present on darkness of world wide web,
overlay network that uses specific authentication or software, or else its not accessible,
deep down the dark web, there is another thing called dark net. which is not exactly a direct part of world wide web, its more likely Peer to Peer connection, mostly an encrypted network that's limited to only a secret group of people, here mostly illegal activities like Drug dealing, human trafficking, Child pornography, organ black marketing, takes place,
And transactions are done with one and only Crypto currencies, like bitcoin, monero, etc.
Monday, 2 April 2018
What is VPN & How Does a VPN Work?
VPN (Virtual Private Network)
Are you wondering what VPN is ? and how VPN works? Learn how VPN makes your Internet connection more secure,
VPN (Virtual Private Network)
it creates an encrypted connection between your computer and one of VPN servers, which Can be located anywhere around the world. You are able to hide your IP address and
your actual location from your ISP (Internet Service Provider) And other Unwanted trackers in Public WiFi or somewhere else.
Or in Other Words
A VPN protects your privacy online by creating a secure "tunnel" between you and your Internet destination.This tunnel is created by first authenticating your client to Your device with a VPN server. The server, which you can run yourself with VPN application installed in your device, then it uses one of several encryption protocols to make sure that everything sent between you and websites and Internet services can't be monitored by trackers. as i said before, It does it by creating an encrypted tunnel, which is like putting a package into a box and then sending it to someone. Nobody can see what it's inside the box until it's opened/decrypted.
An encrypted VPN tunnel diagram - image credit: Check Point Software.
Reasons, why should you use a VPN:
- Enhanced security. When you connect to the network through a VPN, the data is kept secured and encrypted. In this way the information is away from trackers
- Remote control. In case of a company, the great advantage of having a VPN is that the information can be accessed remotely even from home or from any other place. That’s why a VPN can increase productivity within a company.
- Share files. A VPN service can be used if you have a group that needs to share files for a long period of time.
- Online anonymity. Through a VPN you can browse the web in complete anonymity. and its the main purpose, the advantage of a VPN service is that it allows you to access both web applications and websites in complete anonymity.
- Unblock websites, Apps & bypass filters. VPNs are great for accessing blocked websites And applications or for bypassing Internet filters. This is why there is an increased number of VPN services used in countries where Internet censorship is applied.
- Change IP address. If you need an IP address from another country, then a VPN server can provide you this.
- Better performance. Bandwidth and efficiency of the network can be generally increased once a VPN solution is implemented. but may be there is a fall in speed sometimes
Sunday, 1 April 2018
Welcome to Dark Web Developers Community
Darkweb Developers is an internet based IT Company, headquartered in West Bengal, India, with operations all over the globe. The company began its journey in the year 2016, it was founded By Sudipta Pramanik, initially it was a Digital marketing Company, later on they expanded to various other disciplines like Financial Consultancy, App Development, Product Design etc.
stay tuned with us for more
.
Subscribe to:
Comments (Atom)
Getting Started with Android Studio
Getting Started: A n d r o i d S t u d i o A journey towards a ndroid d e v el opm e nt Android Studio by darkweb develop...

-
You might have noticed these days, People around are talking about Dark webs Deep webs Surface webs etc. etc. do you know whats' th...
-
VPN ( V irtual P rivate N etwork) Are you wondering what VPN is ? and how VPN works? Learn how VPN makes your Internet connection...









